Target’s Cybersecurity team believes in the idea that “security is a team sport.” It’s not just something we say, it's a principle we champion that guides our work and something we believe makes us stronger together. Though it’s been a guiding principle for a long time, the notion of security as a collaborative effort is critical today, as organized retail crime has skyrocketed in recent years and continues to worsen. Retailers don’t have the luxury of time to figure out a problem of this magnitude by themselves, making cooperation with others in the industry, community, law enforcement, and government partners a vital element in stopping these bad actors.
Criminal groups continue to strengthen their capabilities to conduct fraud seamlessly across digital and physical landscapes. Lines are blurring between cyber threats, online fraud, and physical loss prevention – not only in Target stores, but industry-wide. These syndicates are better organized than previous threats. They collaborate with one another to take advantage of retailers on an international scale. According to the National Retail Federation, organized retail crime cost retailers and communities $95 billion in 2021, up from $90 billion in 2020. It is now more important than ever for retailers to come together to build teams and develop technology to help combat these situations, and to use our knowledge of cyber principles to combat fraud.
Stronger Together
All companies need to adapt constantly to the rapidly evolving cyber threats we face. An effective way to combat these threats head-on is through collaboration. One way in which we collaborate in the industry is through our membership in the National Retail Federation (NRF), the world’s largest retail trade association. We recently worked with the NRF to form a group focused on sharing information to help us all with combating fraud. This group is unique as it unites retail leaders from cross-functional groups like cybersecurity, assets protection, finance, law, artificial intelligence, and others whose job responsibilities include working to fight fraud. We focus not on our partners’ titles but on the work that they do and collaborate on the issues we notice in our own locations to help each other with identifying trends and changes in the threat landscape. By working closely with industry partners, we share information and improve our companies’ defenses while also improving cybersecurity capabilities for the entire retail industry.
I recently attended the NRF PROTECT conference, an event focused on bringing retail teams together for a day of discussion on the continually evolving threats we are seeing in the industry, and how we can face these threats together. I shared how our team is working to build custom technology that can be used to both enhance security and customer experience. In that spirit of collaboration, I wanted to share some of the main areas of focus we discussed with our retail partners that day, including how engineers can get involved in these areas even if they’re not already on a cybersecurity team.
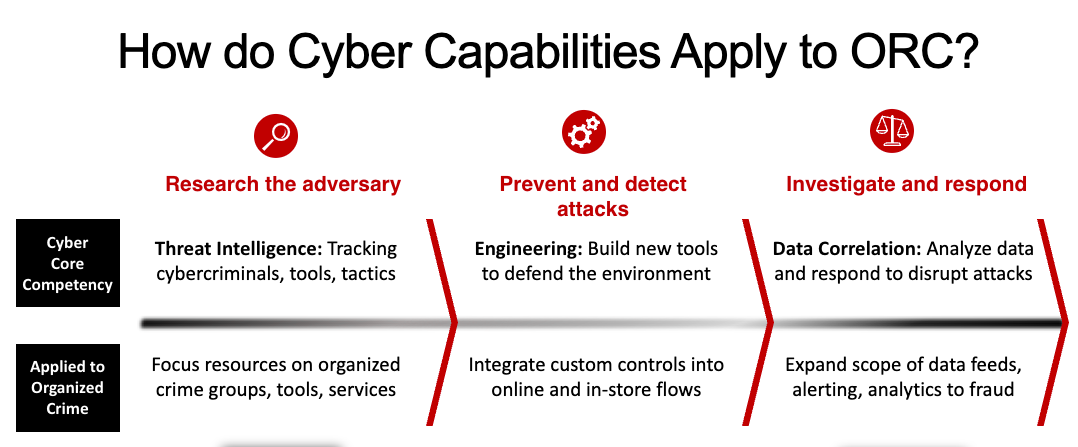
Applying Cyber Capabilities to Organized Retail Crime
Over the last few years, the shopping patterns and needs of consumers changed significantly and many adjusted their preferences to online or contactless experiences like Drive Up. We always want to ensure we are a safe and easy place for our guests to shop, regardless of how they like to shop. While we’ve worked hard to make things as easy as possible for our guests, fraudsters quickly adapt, trying to take advantage of what they view as new opportunities. We needed our team to adapt our processes to put up the right roadblocks and friction to stop bad actors both in store and online.
However, our ultimate goal is to strike the right balance between adding friction and roadblocks for bad actors while keeping the experience smooth and as friction-free as possible for our guests and team members. This presents a unique challenge to our technology and store teams to work in tandem on these issues. As the bad actors moved seamlessly from digital to physical activities, we needed to do the same to disrupt them. Our cybersecurity team assumed the responsibility for fraud mitigation by working closely with our assets protection team. We take a three-pronged approach to these issues which includes researching our criminal adversaries, preventing and detecting attacks, and investigating and responding accordingly. We see our approach paying off in a number of different scenarios that blend between our online and store experiences. Here are a few examples of how our teams apply threat intelligence, detection, and response to fight fraud.
Returns Fraud
We build custom fraud mitigation solutions into the returns flow, enabling us to identify when the transaction is likely a guest versus a bad actor. This allows us to continue to elevate the guest experience without having to add additional friction in front of everyday guests to stop any fraud tactics we see. In cyber, we are intel-driven. We study attackers and their tactics, techniques, and procedures (TTPs) to build targeted blocks, detection, and response. This same approach can be effective when applied to combating retail fraud.
Retail fraud rings tend to operate right out in the open. They don’t hide out on the dark web, but instead have professional websites and are active on social media, engaging constantly with “customers.” Some even have their own merch! All of these make it helpful for us to identify them, but one of the things they do to make it even easier for companies to track their behavior is they sell handbooks detailing how to successfully conduct fraud in stores against retailers like Target. We study those tactics that we can then inform our teams on how best to block them, just as we would defend against bad actors online.
Studying and knowing about these fraud patterns is the key. We look for indicators that don’t match normal shopping and return patterns. This surfaces anomalous behaviors so we can build rules from patterns that don’t align to typical guest behaviors. Our team’s engineering acumen allows us to build custom solutions from the patterns we observe to stop the bad actors in their tracks. Building and using our own products allows us to adjust quickly when we observe changes in behavior. We might not have this agility with an external vendor solution.
Resellers and Bots
Our Cyber Defense team was already well-positioned to address bots and resellers at the onset of the pandemic when the e-commerce industry saw an intense spike in automated traffic by way of “reseller bots.” These bots are designed to scrape inventory-related data from websites and purchase excessive quantities of high-demand products with the intent of then selling these products on secondary markets at steep price markups. As a result, consumers were frequently left to deal with mass inventory shortages and severe price-gouging.
Starting with items like hand sanitizer and toilet paper, resellers quickly took advantage of the new demand driven by the pandemic. Eventually, hot items shifted to include gaming consoles, trading cards and other collectibles. Due to the sudden, bot-driven spike in consumer demand for these products and exponential increases in traffic, we knew we had to work quickly to protect Target.com to ensure overall site stability, but also to ensure our guests could get the products they truly wanted while maintaining a positive guest experience for them. We had been dealing with bots and automated activity related to other common web-based attacks for years and built multiple layers of defense to combat this activity. To tackle this increasingly aggressive problem, we leveraged our experience and defense-in-depth approach, while partnering closely with other Target teams focusing on fraud, site reliability, and guest experience to ensure our strategies and approaches aligned.
With our cyber and fraud teams collaborating closely, we had access to broader data sets and a more holistic feedback loop to keep improving our detection and prevention capabilities. If we weren’t able to block automated activity prior to it hitting Target.com, we could rely on the additional layers of scrutiny based on our research of normal guest activity and normal guest login behavior. This included checking for indicators of fraud or abuse at the time of checkout to ensure that the fraudulent transactions were not allowed to be processed.
Along the way, we celebrated the wins at headquarters when reseller bot actors posted online about difficulties getting products from Target and celebrated even more when our guests would post on social media about how happy they were to have secured a gaming console or other hot item from Target. To quote one of our guests, “I enjoy seeing continued efforts to eliminate the use of bots and mass bulk purchasing – so that everyone has a chance to enjoy hot products.” This guest-first mentality really applies everywhere at Target and the team remains passionate about helping our good guests continue to get the products that they need.
Applying Learnings
First of all, no matter your organization’s size, complexity, or structure, you can start working more effectively across digital and physical fraud mitigation efforts. You don’t have to reorganize or build a huge team, but you do need to learn to work cross-functionally across capabilities, just like the bad actors do. Behaving like one team is key and working towards alignment with your partners on teams like cyber defense, and assets protection, physical security, or fraud can allow you to align and share vital information with one another. Alignment is important as it mirrors the ways in which fraud actors are collaborating, sharing information, and constantly crossing between physical and digital worlds.
My second takeaway would be the importance of being intel and data driven. Correlating disparate data across enterprise teams has been the best way we have found to find patterns and connections to identify repeat fraud that helps us build custom technology solutions that we use to stop this behavior oftentimes before it starts or interrupt it before it causes disruption to our guests or team members. Building strong preventative controls and strong detection models can only be made better by improved access to wider data sets across the company.
Finally, focus on getting more proactive. Individual case investigation is a foundational component of a successful cyber program, but the most beneficial learning of all is figuring out how not to repeat the same case twice. Each case will show you what abuses the bad actors are conducting and give you the insights you need to stop the abuse in the first place. This is where strong engineering practices come into play as teams can build custom fraud and abuse tools directly in line with the services these bad actors are abusing. Adjusting your defenses quickly is essential, as fraudsters pivot their tactics, and being able to respond rapidly to write new rules based on new fraud is a differentiator.
As we continue to fight back against organized retail crime in partnership with our peers in the retail industry, we are always looking for engineers who like to build custom solutions. We love giving back to the Open Source community with contributions that that help others stay strong in their own fight against cyber crime. Click here to see current job openings on our team – we'd love to have you join us in our ever-evolving fight against cyber crime and fraud.
RELATED POSTS
Synthetics: Continuous Assurance of Detection Components
By undefined, December 13, 2022
This post provides a solution for utilizing synthetic events for the purpose of validating signature integrity and functionality, with the goal of achieving continuous assurance of a system’s detection signatures.